Understanding Microsoft Defender for Containers features – Onboarding Containers
Microsoft Defender for Containers is a cloud-based solution designed to safeguard your containerized environments. It protects your clusters whether they’re running in Azure Kubernetes Service (AKS), Amazon Elastic Kubernetes Service (EKS) in a connected Amazon Web Services (AWS) account, Google Kubernetes Engine (GKE) in a connected Google Cloud Platform (GCP) project, or other Kubernetes distributions (using Azure Arc-enabled Kubernetes). Defender for Containers brings with it the three core aspects of container security, which are as follows:
- Environment hardening: As stated previously, Defender for Containers safeguards your Kubernetes clusters regardless of whether they are operating on Azure Kubernetes Service, on-premises or infrastructure as a service (IaaS) Kubernetes, or Amazon EKS. Container Sentry offers ongoing assessments of clusters, delivering enhanced visibility into misconfigurations and supported with actionable guidelines to mitigate identified threats.
- Vulnerability assessment: It also supplies vulnerability assessment for images stored in Azure Container Registry and Elastic Container Registry (ECR).
- Runtime nodes and clusters protection: Alerts are generated by the threat protection system for both clusters and nodes, signaling potential threats and suspicious activities.
Let us now understand the Defender for Containers architecture diagram.
Defender for Containers architecture diagram
Defender for Containers is developed differently for each Kubernetes environment. The links in this section give you the detailed and updated architecture diagram for each Kubernetes environment.
Azure Kubernetes Service (AKS)
When safeguarding a cluster hosted in AKS, Defender for Cloud ensures a seamless and effortless process for collecting audit log data without the need for an agent. The deployment of the Defender profile on each node enables runtime protections and helps the collection of signals. For more comprehensive information, please consult the Microsoft documentation (https://learn.microsoft.com/en-us/azure/defender-for-cloud/defender-for-containers-architecture?tabs=defender-for-container-arch-aks#architecture-diagram-of-defender-for-cloud-and-aks-clusters).
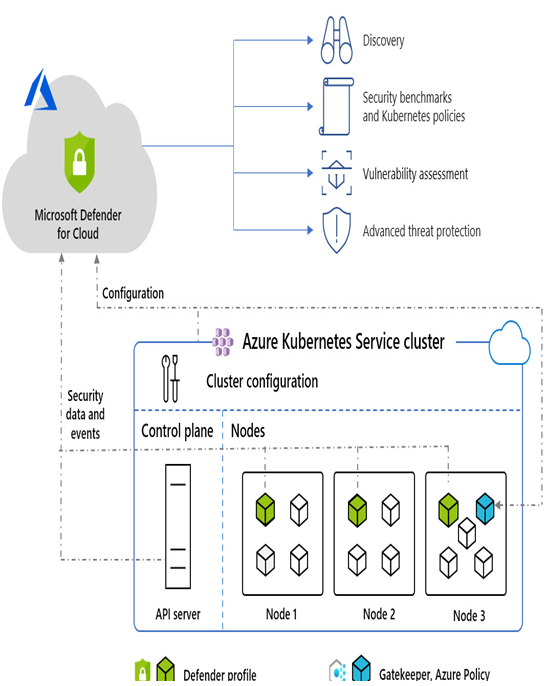
Figure 7.1 – Architecture diagram of Defender for Cloud and AKS cluster (source: Microsoft)
Arc-enabled Kubernetes clusters
When a non-Azure container is integrated with Azure through Arc, the Arc extension collects Kubernetes audit logs from every control plane node within the cluster. Subsequently, the extension transmits the log data to the Microsoft Defender for Cloud backend in the cloud, enabling comprehensive analysis. Although the extension is associated with a Log Analytics workspace used as a data pipeline, the audit log data itself is not stored within the Log Analytics workspace.
For more details and updated information on this, refer to your chosen CSPM vendor documentation or, in this case, the Microsoft documentation (https://learn.microsoft.com/en-us/azure/defender-for-cloud/defender-for-containers-architecture?tabs=defender-for-container-arch-eks#architecture-diagram-of-defender-for-cloud-and-eks-clusters).
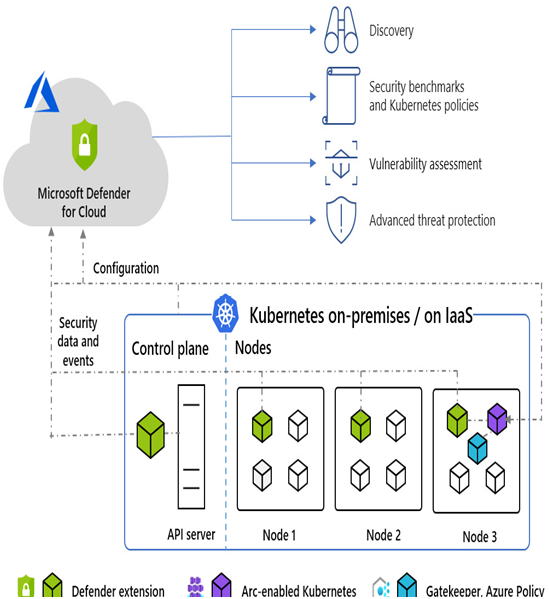
Figure 7.2 – Architecture diagram of Defender for Cloud and non-Azure cluster (source: Microsoft)
