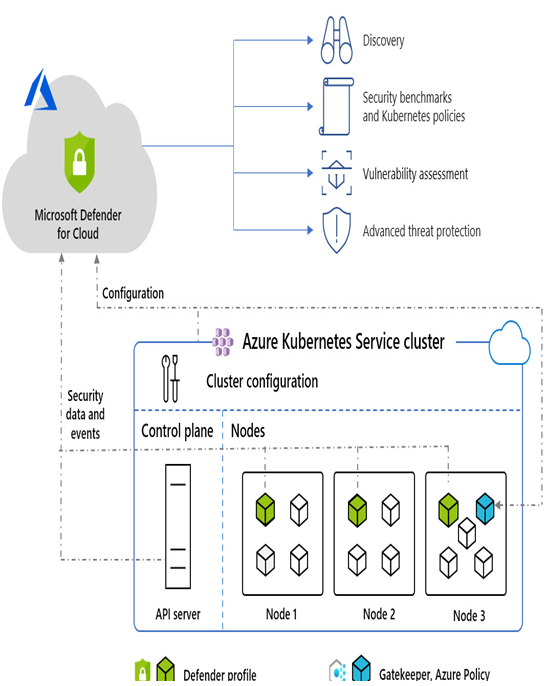
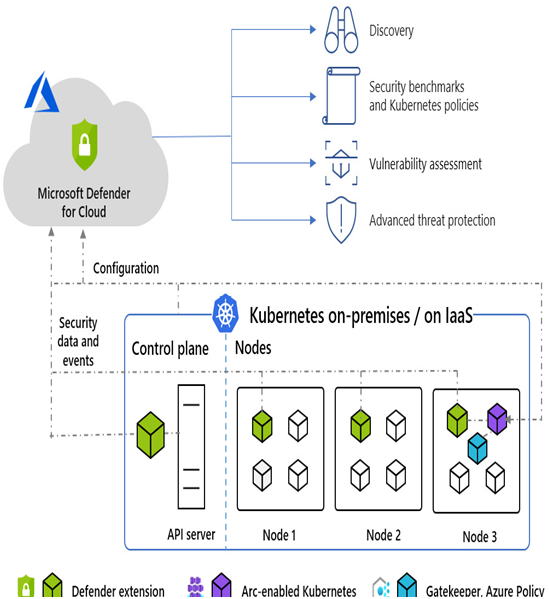
Let’s look at some challenges:
- Log volume and storage: CSPM tools generate a significant volume of log data, especially in large-scale environments. Managing and storing this data can be a challenge, requiring adequate storage capacity and efficient log management practices.
- Log integrity and protection: Ensuring the integrity and protection of log data is essential. Unauthorized access or tampering with logs can undermine the reliability and accuracy of the audit trail.
- Log retention and compliance: Compliance requirements may dictate specific log retention periods. Managing long retention policies and ensuring compliance with regulatory guidelines can be challenging, especially in complex or highly regulated environments.
Best practices for activity logging
Here are a few best practices:
- Log aggregation and centralization: Aggregate logs from various sources within the CSPM environment into a centralized logging system. Centralized logging simplifies log management, analysis, and correlation.
- Log format standardization: Standardize log formats and structures to facilitate log analysis and correlation across different CSPM tools and systems. Adhering to common log formats simplifies log management and enables better interoperability with log analysis tools.
- Secure log storage: Implement secure log storage mechanisms to protect log data from unauthorized access or tampering. Encrypt log data at rest and in transit and restrict access to logs based on PoLP.
- Log retention and rotation: Define and adhere to log retention policies based on compliance requirements. Implement log rotation practices to manage log volume and ensure optimal storage utilization.
- Log analysis and monitoring: Establish processes and tools for log analysis and real-time monitoring. Proactively analyze log data for anomalies, security incidents, or policy violations to identify potential threats or vulnerabilities.
- Integration with SIEM/log management systems: Integrate the CSPM tool’s activity logs with SIEM or log management systems. This integration enhances the correlation and analysis of log data with other security events across the infrastructure.
- Regular log reviews and audits: Conduct regular log reviews and audits to detect any suspicious activities, identify patterns, and ensure compliance with security policies and regulatory requirements.
- IR and forensics: Leverage activity logs for IR and forensic investigations. Detailed logs can provide critical information for root cause analysis (RCA), impact assessment, and identifying remediation actions.
By carefully considering the aforementioned challenges and best practices, you can gain valuable insights into the cloud environment, identify potential security threats or compliance issues, and respond effectively to incidents or breaches. These logs are essential for security monitoring, IR, forensic investigations, and overall cloud infrastructure governance.
Summary
Setting the CSPM environment is a crucial procedure for tools as it establishes the foundation for effective CSM. In this chapter, we delved into crucial topics such as user management, permissions settings, integrations with other tools, reporting capabilities, challenges, and best practices to overcome challenges. In the next chapter, we will deep dive into cloud asset inventory.
Further reading
To learn more about the topics that were covered in this chapter, take a look at the following resources:
- Key requirements of a modern CSPM (https://www.wiz.io/academy/what-are-the-key-requirements-of-a-modern-cspm)
- How Gartner Defines CSPM and 3 Tips for Success (https://www.aquasec.com/cloud-native-academy/cspm/gartner-cspm/)