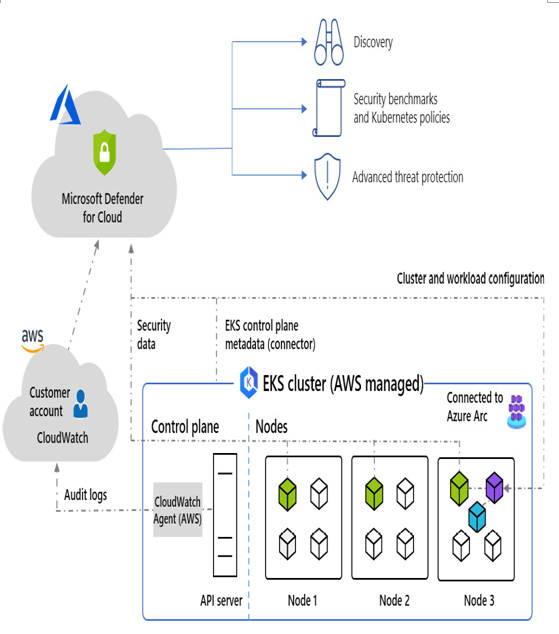
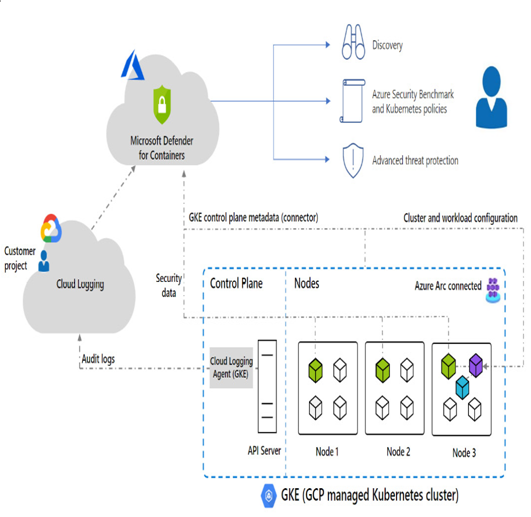
Container security and CSPM are areas that continue to evolve and advance as technology progresses. Here are some of the most recent trends and future advancements to watch for in container security and CSPM:
- Enhanced container image security: There has been an increased focus on improving container image security by integrating advanced scanning techniques, machine learning, and artificial intelligence (AI). This will help identify even more complex vulnerabilities, malware, and supply chain attacks.
- Runtime protection and behavioral analysis: Container runtime protection will evolve to include more advanced behavioral analysis and anomaly detection capabilities. This will enable the detection of suspicious activities and real-time mitigation of threats during container runtime.
- Kubernetes-native security solutions: As Kubernetes remains the dominant container orchestration platform, there will be a rise in Kubernetes-native security solutions. These solutions will provide tighter integration with Kubernetes, offering enhanced visibility, configuration management, and automated remediation for Kubernetes-specific security risks.
- Immutable infrastructure: The concept of immutable infrastructure, where containers are treated as disposable and immutable, will gain more traction. This approach simplifies security management by minimizing the attack surface and reducing the impact of security incidents.
- Compliance automation: CSPM tools will increasingly automate compliance monitoring and reporting processes. This will help organizations align with various regulatory frameworks by continuously assessing the security posture of their container environments and generating compliance reports.
- Integration with DevSecOps: Container security and CSPM solutions have seamlessly integrated with DevSecOps practices and toolchains. This integration enables security to be embedded throughout the software development life cycle, ensuring security and compliance from the initial stages of application development.
- Zero trust architecture: Zero trust architecture, which assumes no implicit trust for any user or container, will be adopted more widely. Container security solutions and CSPM tools will incorporate zero trust principles to enforce strict access controls, authentication, and authorization mechanisms.
- Serverless security: As serverless computing gains popularity, container security solutions and CSPM tools will adapt to address the unique security challenges of serverless environments. This includes securing serverless functions, managing access rights, and monitoring functions for vulnerabilities or misconfigurations.
- Threat intelligence and threat hunting: Container security solutions and CSPM tools will leverage threat intelligence feeds and advanced threat hunting techniques to proactively identify emerging threats and indicators of compromise. This proactive approach will help organizations stay ahead of potential attacks.
- Continuous integration and continuous delivery (CI/CD): Container security and CSPM solutions will integrate more seamlessly with CI/CD pipelines to enable automated security testing, vulnerability scanning, and configuration checks during the application build and deployment stages.
Staying current with the latest developments in container security is essential to maintaining the security of containerized applications and infrastructure.
Summary
In this chapter, we understood containerization and explored its benefits in the context of CSPM by explaining the concept of containerization, which involves encapsulating an application and its dependencies into a portable and isolated unit called a container. We also discussed unique container security challenges, onboarding containers to CSPM tools, particularly in the context of Microsoft Defender for Cloud, and challenges that may arise in the onboarding process. We also delved into security best practices for containers and the most recent trends and advancements in container security in the context of CSPM.
In the next chapter, we will discuss CSPM tool environment settings and integration with other IT tools.
Further reading
To learn more about the topics that were covered in this chapter, take a look at the following resources:
- Secure Your Containers with Confidence: https://start.paloaltonetworks.com/container-security-101-understanding-the-basics-of-securing-containers
- Scan registry images with Microsoft Defender for Cloud: https://learn.microsoft.com/en-us/azure/container-registry/scan-images-defender?source=recommendations
- Containers support matrix in Defender for Cloud: https://learn.microsoft.com/en-us/azure/defender-for-cloud/support-matrix-defender-for-containers